Sketchy Emails Are Everywhere! Here’s How to Not Get Phished

Phishing isn’t just a tech term; it’s a real threat. And if you’ve been keeping tabs on the news cycle, you’ve likely seen countless stories about the uptick in phishing attacks. Google Docs got phished. The dreamy new French president got phished. And turns out, even the 2016 election got phished.
But here’s the really crazy part.
For every attack that’s publicized, there are so many more that go undetected and unreported.
So what the heck is phishing? And why did it become the darling of the hacking world? We’ll explain all that and, most importantly, what you can do to keep your data safe in a world that’s literally gone phishing.
Leave migrating your site, installing WordPress, managing security and updates, and optimizing your server performance to us. Now you can focus on what matters most — growing your business.We Make WordPress Easier for You

What Is Phishing?
Phishing is when cyber criminals use legitimate-looking emails, websites, or even phone systems to trick people into surrendering their sensitive data. This can include personal information like the content of your emails, credit card numbers, bank account numbers, or even password credentials.
Phishing scams are particularly dangerous because they look legit! Cyber criminals use very similar design elements and copy to mimic the look of emails sent from legitimate companies or sources.
Say a scammer is trying to gather credit card numbers. They could send a phishing email that looks like it came from PayPal, a legitimate online payment system, which urges you to enter your login info. You type in your username and password, and now the cyber criminal has all they need to siphon off your hard-earned cash.
Related: Worried About Hackers? Here’s What You Can Learn From These Crazy Election Cybersecurity Issues
Types of Phishing Attacks, Explained
Since it’s pretty easy to fall victim to a phishing attack, it’s important to be aware of the different types of scams criminals use to steal your information.
Spear Phishing
It’s not as sporty as it sounds. Instead of sending the generic Nigerian-prince message we’ve all encountered since the dawn of the internet, spear phishing scammers take the time to review the data you’ve willingly put online, for example, on Facebook or Twitter. Pairing that information with your friend list, the hacker will customize an email that appears to be from someone you know and trust.
Clone Phishing
Clone phishing scams are particularly tricky to identify because cyber criminals clone a legitimate email message or email address that has previously sent you an attachment. Then they replace the attachment with a malicious virus or download. On first glance, the cloned email looks exactly like one you’ve previously received from a trusted source. This type of attack is usually used to allow a hacker to gain control of your device.
Whale Phishing
Whale phishing, also known as whaling, is an apt name. The scammers behind these types of attacks are hunting bigger fish than you and me. They could be aiming to access confidential company information, emails from a political party, or private photos of celebrities.
Whaling with Ransomware
Remember in Season 6 of The Good Wife when Diane Lockhart opened an email attachment from her trusted partner, but it ended up being ransomware from a Russian hacker who threatened to delete all their files unless they paid up? Well, that happens in real life too. Recently, we’ve seen a spate of television shows and movies stolen by hackers hoping to cash in on threats to release the must-watch content early. These types of attacks account for 93 percent of phishing scams today.
Related: 13 of the Best Security Plugins to Keep Your WordPress Site Safe
How Can Phishing Hurt Your Website?
If you own a website and accidentally fall victim to a phishing scam, it’s okay to be worried. Why? Because there’s a lot on the line. When a hacker gains access to your website, they can effectively:
- Steal client information
- Hijack usernames and passwords
- Take money from your business and clients
- Make unauthorized purchases
- Add themselves as a website administrator to incite future attacks
- Gather sensitive information
- Auction your sensitive information
- And even more nefarious things than we can list here.
9 Ways to Spot Phishing Attacks
The best way to not have to clean up after a phishing attack is to not take the bait in the first place. Educating yourself (like you’re doing right now; go you!) and then staying up to date on the latest iterations of phishing scams is critical. Then, you should follow these nine tips when an unexpected message pops up into your inbox.
- Ask yourself if you are expecting an email of this nature. Did you request a password reset or not? Did you book a hotel, or is this an unwarranted confirmation email? Did you discuss a wire transfer with a bank or client previously? If the answer is no, then proceed with a heap of caution.
- Even if you recognize the name of the business sending you an email — think PayPal, Google, or Facebook — ask yourself if you currently interact with the organization.
- Are they asking for personal information? Legitimate businesses don’t ask for social security numbers, bank account info, or password credentials over email.
- Are you expecting an attachment from a client or a corporation? If not, don’t open the attachment, especially if it is from a company or individual you don’t recognize.
- Is the email asking for sensitive information? If a message asks for personal information about you, a loved one, a friend, or a coworker, avoid it.
- What do the links look like? Do they actually look like links normally sent from the company you do business with? Review them before clicking.
- Review the “From” email address for any inconsistencies.
- When you click “Reply,” does the “To” field match the sender information?
- Pay attention to design and grammar. Often phishing scams are close in appearance and language to a legitimate company email but not quite right. If you notice the design is slightly off or there are several misspellings, report the email to your service provider.
When you make a habit of carefully reviewing your emails, you’ll be far less likely to fall victim to a sketchy one.
Where Can You Report Phishing Attempts?
If you believe you have been sent a phishing scam, take the time to report it. Forward deceptive messages to:
- The Federal Trade Commission at spam@uce.gov. Make sure you forward the complete spam email, including subject line.
- Your email provider.
- The organization that the scammer is impersonating. Most companies have a specific email address for these type of messages.
- The Anti-Phishing Working Group, a consortium of ISPs, security vendors, financial institutions, and law enforcement agencies with a common database, at reportphishing@antiphishing.org.
DreamHost customers should also reach out immediately if they’ve seen anything “phishy” going on.
- If you believe that fraudulent activity is occurring in conjunction with a DreamHost account, please contact DreamHost and let an abuse support rep know. Please provide as much detail as possible.
- If the fraudulent activity involved the use of email, please be sure to include the full headers and content of that email as well.
- If your credit card was fraudulently used to sign up for a DreamHost account, please provide the first 2 and last 4 digits of the card, name, date, and the amount of the transaction.
In the event you clicked on a link from a phishing scam or sent sensitive information through a phishing scam, make sure you immediately change all of your usernames and passwords, change your credit card information, and protect yourself against identity theft.
Related: Why Security Through Obscurity Isn’t Enough to Keep Your Website Safe
A Phishing Case Study, DreamHost Style
Unfortunately, phishing isn’t going away anytime soon, and cyber criminals are only getting more sophisticated. Does this mean you should run away, hide, and never use email or a computer again? No! Instead, let’s practice everything you just learned about phishing with a DreamHost case study. Imagine getting an email that looks like this:
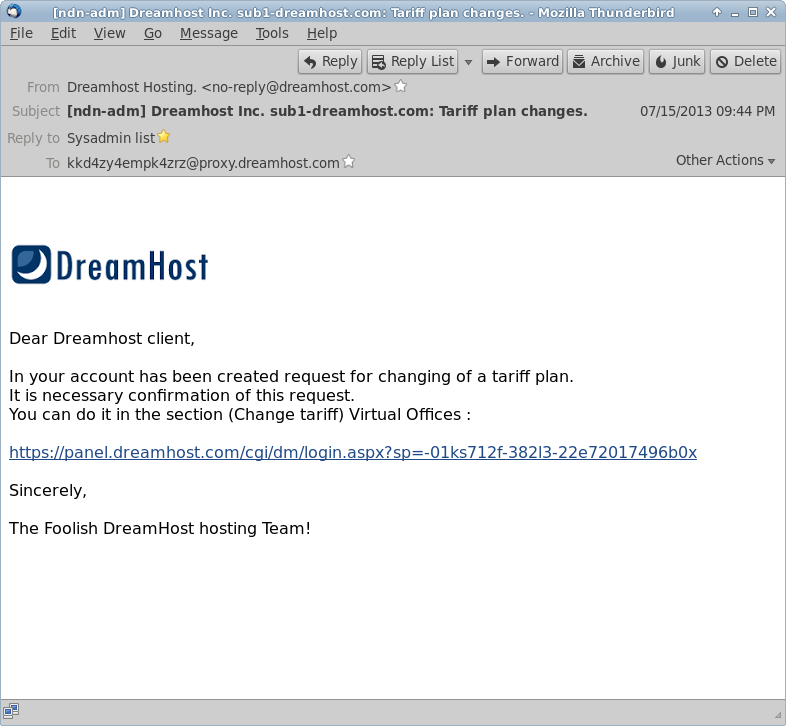
It looks legitimate, but I don’t remember initiating anything tariff related in my account, so let’s follow the link to log in and see what they mean. Let’s log in and see what the fuss is about.
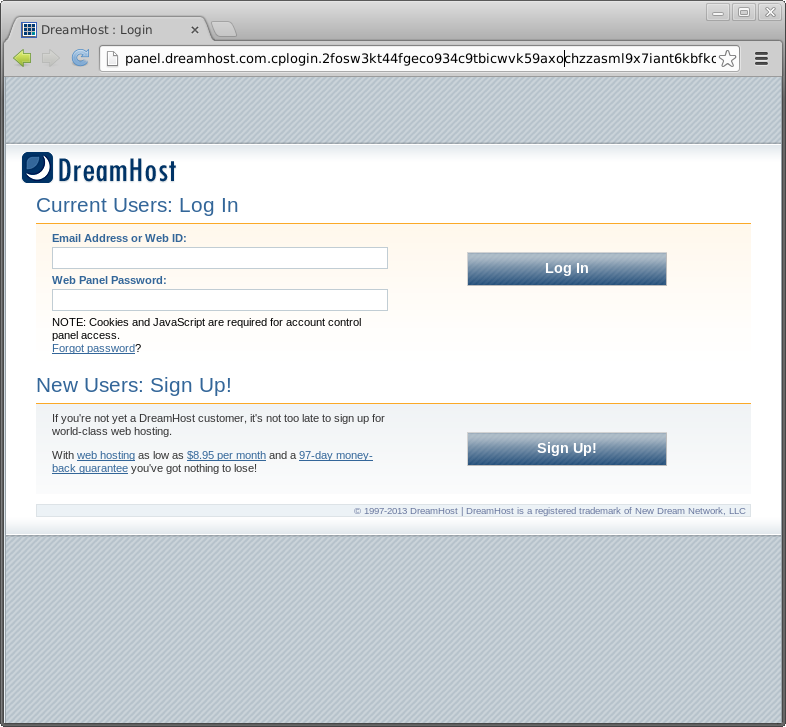
Guess what? If you logged in, you’ve just been phished. So instead of giving the hackers what they want, let’s go back in time and examine the email.
If you didn’t notice the first time around, the “To” field looks pretty odd and isn’t directed at your specific email address. Some companies do this to keep their users private if they’re sending to a large list, but this still looks extra sketchy.
The email also addresses you as a generic “DreamHost client,” instead of by name, which many companies — including us — do.
Now, let’s take a look at the link. They were nice enough to write it all out for us in the email, but where does it actually go
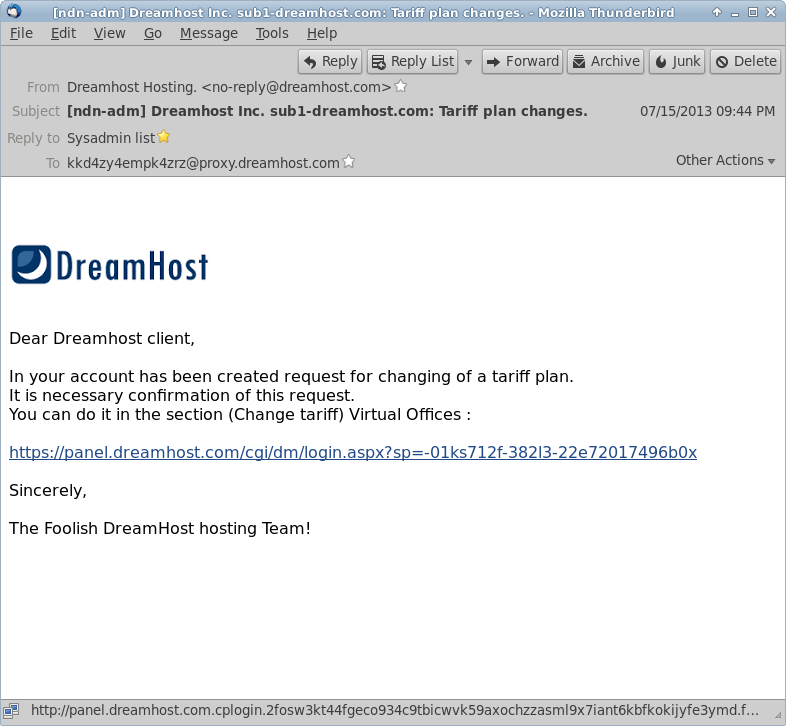
By hovering over the link, we can see the actual address of the link in the very bottom of the window. That doesn’t look right at all!
First, you should never log into a page that has HTTP instead of HTTPS. The difference is an unsecured versus a secured connection.
Second, there’s all sorts of gibberish after the .com that doesn’t match the link in the email. If that isn’t a dead giveaway, pull up panel.dreamhost.com in a new window. You’ll see it looks totally different.
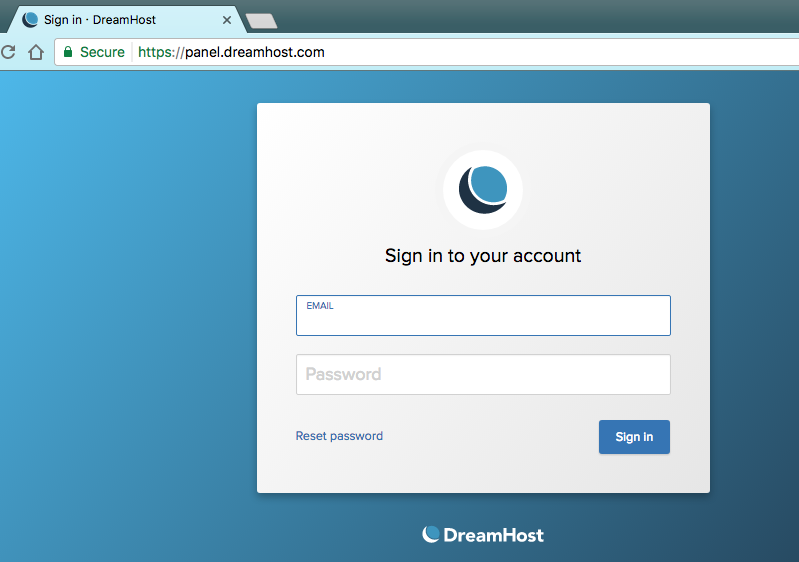
Crisis — and data theft — avoided. Nice work!
Have Solid Advice for Avoiding Phishing Scams?
Now that we’ve outlined the essentials for spotting scams, we want to hear from you! How do you avoid phishing scams? And what do you make of the uptick in high-profile attacks? Help your fellow cyber-crime warriors by sharing your experiences in the comments below.
—Case study by Kevin Stanonik